The Internet of Things (also called the Internet of Everything) is essentially about connecting conventional objects and sensors to the Internet, transforming them from ordinary items into "smart" devices. Some examples include connected cars, thermostats, refrigerators, wearables and televisions. What's staggering is how quickly IoT emerged since the term was coined in 1999. After Gartner listed it as a new emerging technology nearly than a decade ago, connected devices have growth to equal more than 26 billion installed worldwide. That number will only continue to grow.

While the opportunities are vast – from improving manufacturing processes, to more efficient response to humanitarian aid crises, to more intuitive healthcare services – there are some notable IoT challenges and risks standing in the way of success. Let’s take a look at the top three below.
1. Cybersecurity Risks
The existence of some glaring security issues with the Internet of Things should not be a shocking revelation. Such risks are now being heavily discussed as momentum builds. It is important to note that hacks now look different from traditional cyberattacks and can bring severe fallout in some cases. As IoT hacks involve tangible objects (rather than data alone), physical damage (e.g., a car being hacked and crashed) can result in addition to malware or identity theft.
Fiat Chrysler and Tesla vehicles experienced car hacks via their infotainment systems in 2015. Both companies quickly offered patches to fix the issues, but these incidents raised awareness about security issues in digitally connected automobiles and even sparked a Senate bill called the Security and Privacy in Your Car (SPY) Act. The Act would require automakers to implement IT security measures in all connected cars. Additionally, the National Highway Traffic Safety Administration (NHTSA) and the Federal Trade Commission (FTC) would be tasked with developing privacy and secuirty standards for vehicle systems and the data they collect.
Another large-scale hack involved Hong Kong-based toymaker VTech. The hack compromised the personal information (including names, home addresses, photos and videos) of more than 6 million children. Read more about the risks of connecting children to the Internet in this Reuters article. This is not the first baby-device hacking that has startled parents around the globe; check out these internet-connected baby monitor horror stories compiled by Buzzfeed.
So, the million dollar question here is: Exactly how much are consumers willing to pay (their privacy, sensitive information, personal safety) for the convenience of a connected world? While companies have a long way to go in terms of establishing network security, consumers bear some responsibility in educating themselves, protecting their data as much as possible and setting limits for what type of information they are willing to provide.
From a product design and development standpoint, a major risk is failing to incorporate (or at least account for) security measures during the design phase and instead realizing the need post-production. Considering product and data security early on is necessary to ensure products are outfitted for both security and interconnectivity. In addition to security software, extra measures such as firewalls, access control and encryption should be considered. It's possible that some devices may not have enough internal memory to support sophisticated security software, which further stresses the need for broader network security.
2. Lack of Universal Architecture
Currently, devices are not operating on a single network, which poses an issue for interoperability. For the IoT to reach its full potential, devices need to be able to properly communicate with one another, as well as the network. Right now, some devices can connect to multiple devices, while some can connect only to manufacturer-approved devices, and others still can connect only to the Internet, not with any other devices. Designing products within a specified architecture would result in two advantages: device compatibility and increased security controls.
One group working to establish this framework is the Open Interconnect Consortium which, according to their site, is “defining the specification, certification and branding to deliver reliable interoperability – a connectivity framework that abstracts complexity.”
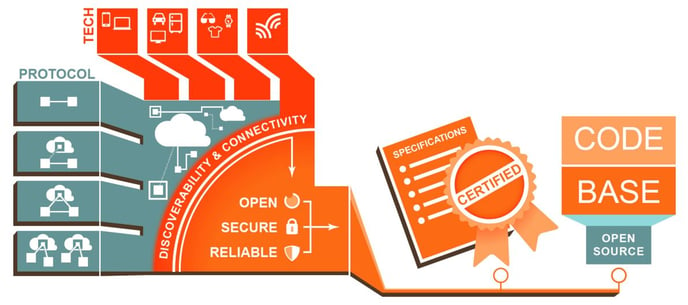
At the rate the IoT is expanding, standardization is long overdue. Companies that build products in a vacuum without considering interoperability will soon find themselves on the outside looking in.
3. No Open Standards
A universal architecture is not where the need for structural development ends. Open standards are also needed for interoperability and network regulation. Many experts, including MIT mechanical engineering professor Sanjay Sarma, who helped lay the foundation for the Internet of Things, believe a degree of government involvement is necessary to develop and implement standards, much like what we saw with the involvement of Defense Advanced Research Projects Agency (DARPA) in the development of the Internet.
Government involvement has also been encouraged by the World Economic Forum. The Forum's 2020 Global Risks report warned that hackers will take advantage of IoT risks unless regulatory and industry groups provide “effective governance.” Collaboration and cooperation will be key to develop such standards and create a safe space for consumers.

Our Advice for Consumers
While industry and government body leaders are sorting out the technicalities, it is inevitable that more connected devices will emerge, and more people will purchase those devices. We have several pointers to help users protect themselves in the meantime:
- Educate yourself about risks. Awareness is crucial to success.
- Protect your devices with passwords. Biometric passwords are best.
- Back up data frequently to prevent loss in the case of a hack or swipe.
- Read user reviews before purchasing a device.
- Read the fine print about how your data will be protected or shared with third parties. Ask the manufacturer to clarify if you have any questions.
- Set limits for how much personal information you are willing to share.




.jpg?width=176&height=56&name=MR_associatedNetwork_logo%20(1).jpg)